|
computer commentary
How well does encryption protect you?Executive summary: not very wellby T. Nelson |

|
computer commentary
How well does encryption protect you?Executive summary: not very wellby T. Nelson |

hatever you think of Eric Snowden's actions, there's no doubt that he got us thinking about computer security again. One of his most significant but overlooked remarks was where he mentioned that the weakest point in an encryption chain is the “end points.” What this actually means is that, even if the information is encrypted, it's easy to recover it by compromising the computers of the sender or recipient.
The government undoubtedly spends some of their billions finding and
exploiting security holes in PCs and servers. As we now know, they also
want to force companies to install backdoors in commercial software. Obviously,
you'll never find an nsa.gov IP in your logs (if you do, it's
almost certainly a fake, just as most of those spams set in koi8-r
are not really from Russia), so we'll probably never know how many
ordinary computer viruses and trojans actually belong to them.
But it's not just end points. Servers are much juicier targets. Based on Snowden's documents, nrc.nl, a Dutch news site, found that the NSA had infected European telecom company servers with malicious software to tap customers' telephone and data traffic.
But as any network guy will tell you, sometimes they don't need to hack in at all. Common practices among even computer-literate users can make secure shell (SSH) and secure sockets layer (SSL) virtually worthless—that is, no better than telnet.
(continued below)
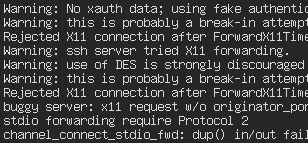
 SSH warning message
SSH warning message
What is happening? I'll use SSH as an example. SSH is good protection against ordinary hackers—the ones who might install a sniffer on your network to capture your traffic—but unless it's used carefully, you could be vulnerable to what is called the man in the middle attack, which is to say a compromised firewall or router.
You might think that no network person would consent to this. But they might not even know. And they're employees, so either they do it or their replacement does it. The place where I work does it as a matter of policy. All supposedly secure connections, they tell me, are intercepted and compromised. You can be sure that most corporate firewalls, and probably many big ISPs, are doing the same thing.
To make encryption work, the two endpoints (let's call them A and Z) must communicate their public keys in advance to each other. That's usually done by a Diffie-Hellman-style key exchange. But in today's Internet, A and Z are usually NATed, which means they aren't even visible to each other. Their IP address is translated by the corporate router, and all the packets you send are fully visible to them. This means the key exchange step, and thus every step following it, are easily compromised.
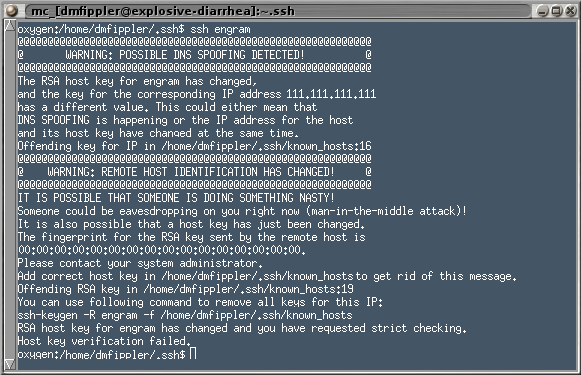
Here is a good description of how this can occur and how to avoid it. They write: “If you connect for the first time to a new server and let ssh accept the host key, you are actually open to a man-in-the-middle attack. However, assuming your DNS isn't spoofed that one time, future connections to this server are safe as long as the server host key isn't stolen.”
A guy named Michael Dundas understands these issues as well. D-H and RSA are well covered in cryptography books, like those written by Bruce Schneier.
Look at the screen shot above. Users of SSH see these warning messages all the time. That's because every time somebody re-installs their operating system, you get the annoying warning about a man in the middle attack, because the key is different. Judging from what I see on Linux discussion boards, I would guess that 99% of users just automatically accept the new fingerprint, delete the old one, and tell the software to accept whatever key comes in.
Now, of course you'd be a fool to send anything sensitive from your work computer. But it may only be a matter of time before ISPs start meddling. So accepting a key over the Internet could be a big mistake. As the saying goes: once compromised, always compromised.
