Silence on the Wire
A Field Guide to Passive Reconnaissance and Indirect Attacks
Michal Zalewski
No Starch Press, 2005, 281 pages

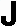 ust when you thought it was safe to go back on
the Internet, Michal Zalewski goes and lists some new ways an
attacker can get information about your computer. It's not
necessary to plant a trojan on someone's Windows computer to
get information; just monitoring their keystroke timing, or
monitoring the LEDs on their modem or network card, Zalewski warns,
can give enough information to make you dangerous. Information is
leaking from your computer and your network in dozens of ways. Even
though analyzing it may only retrieve a fraction of a bit from each
packet, it can greatly reduce the search space for cracking a user's
ssh session. Passive fingerprinting can also be used to track users
and map out even the most well-protected network. Zalewski also
describes, in non-technical terms, his original research that
showed how to use strange attractor analysis of IP initial sequence
numbers to identify a user's operating system, which could lay the
groundwork for an attack. Zalewski was well known on the Internet in
security mailing lists like Bugtraq back in the days when it was
useful; although it's not really a field
guide, this well-written but relatively nontechnical book uses a
narrative, jargon-free style to introduce new network administrators
to a class of security problems that they might not have considered.
ust when you thought it was safe to go back on
the Internet, Michal Zalewski goes and lists some new ways an
attacker can get information about your computer. It's not
necessary to plant a trojan on someone's Windows computer to
get information; just monitoring their keystroke timing, or
monitoring the LEDs on their modem or network card, Zalewski warns,
can give enough information to make you dangerous. Information is
leaking from your computer and your network in dozens of ways. Even
though analyzing it may only retrieve a fraction of a bit from each
packet, it can greatly reduce the search space for cracking a user's
ssh session. Passive fingerprinting can also be used to track users
and map out even the most well-protected network. Zalewski also
describes, in non-technical terms, his original research that
showed how to use strange attractor analysis of IP initial sequence
numbers to identify a user's operating system, which could lay the
groundwork for an attack. Zalewski was well known on the Internet in
security mailing lists like Bugtraq back in the days when it was
useful; although it's not really a field
guide, this well-written but relatively nontechnical book uses a
narrative, jargon-free style to introduce new network administrators
to a class of security problems that they might not have considered.
